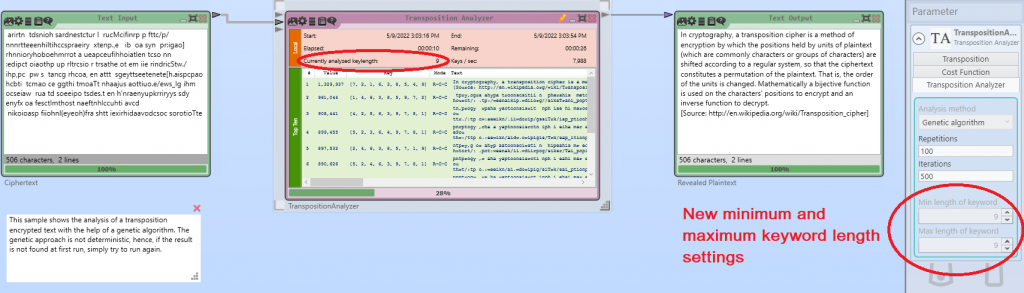
In the last view days, I implemented the Mexican Army Cipher Disk and its cryptanalysis in CrypTool 2. I also made a YouTube video about that (see below in this blog post).
The Constitutionalists in Mexico used the Mexican Army Cipher Disk at the beginning of the 20th century during the Mexican revolution. It is a homophonic substitution cipher, but rather weak. For encrypting a letter, you have either a 3-symbol or a 4-symbol homophone group, with a total of 100 homophones (01 to 00).

The groups are created using the disk device, which consists of 5 disks (see shown figure above):
• The outer disk contains the Latin alphabet
• Four inner disks contain 2 digits numbers
• Four inner disks can be turned
The key of the cipher is the rotation of the four inner disks and can be described in two ways:
1) The digit groups below the letter A : 01, 27, 53, 79
2) With four Latin letters ; each letter is the one above the first digit group of the corresponding disk: A, A, A, A
Build your own Mexican Army Cipher Disk
Now, if you want to also build your own cipher disk, you may use my self-created template here:
Since I used powerpoint to create the template, the angles are not 100% perfect, but it still works well. You need to print it five times and always cut a smaller disk out of each printout. To get more stability, you may also use some cardboard and glue the disks onto these before assembling the device. Finally, all the disks are placed on top of each other. I used a paper clip that I bent and put through all the slices.
Cryptanalysis
If we want to break the Mexican Army Cipher Disk, it is a rather easy task. By hand, we just search in each number group (01 to 26, 27 to 52, 53 to 78, and 79 to 00) for the most frequent homophone. This stands probably for the letter E. Move your disks to all found E positions and you should be able to decrypt your ciphertext.
If you don’t want to break it by hand, you can use CrypTool 2 and the “Mexican Army Cipher Disk Analyzer” component for automatic cryptanalysis. It performs a brute-force attack and searches through all disk settings. Here, with the help of a language model (e.g. English pentagrams) it scores each of the decrypted texts. The correct plaintext should be on the first position of the best list of the analyzer.
YouTube Video
I alse created a YouTube video about the Mexican Army Cipher Disk. You may watch it here:
Some References
- Angel Angel, José de Jesús, and Guillermo Morales-Luna. “Cryptographic Methods During the Mexican Revolution.” Cryptologia 33.2 (2009): 188-196
- Kahn, David. The Codebreakers: The comprehensive history of secret communication from ancient times to the internet. Simon and Schuster, 1966.
- You may also have a look at “kryptografie.de”, which has a nice implementation of the device in the browser: https://kryptografie-de.translate.goog/kryptografie/chiffre/mexican-army-cipher-wheel.htm?_x_tr_sl=de&_x_tr_tl=en&_x_tr_hl=de