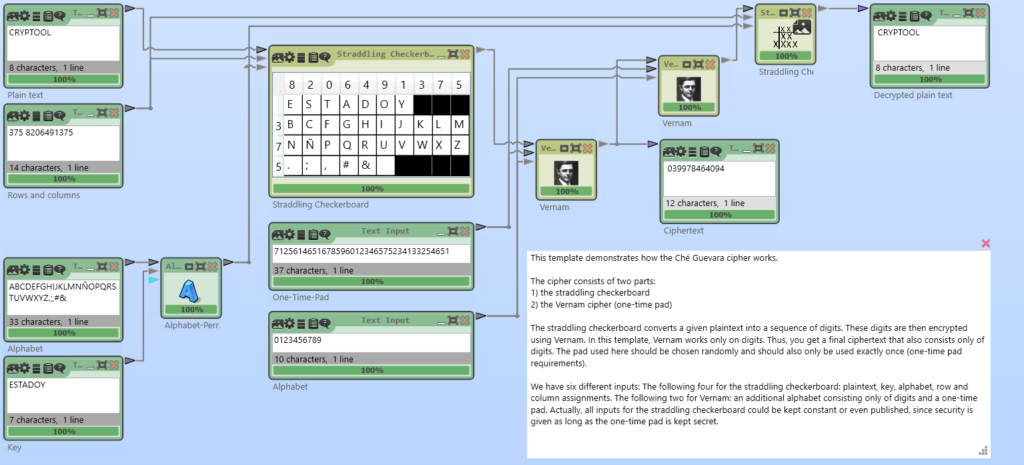
Some years ago, I supervised a bachelor project with the topic “image processing” at the University of Kassel (when I was working for the “Applied Information Security” group). The bachelor students had to implement image processing components in CrypTool 2.
One result of the project was the so called “ImageHash” component. One of my students implemented the “block hash” by Steinebach [1]. It is a robust (or perceptual) hash function, that allows to use it for the search for images in image databases, even when the image is different (e.g. resized or modified) from the original.
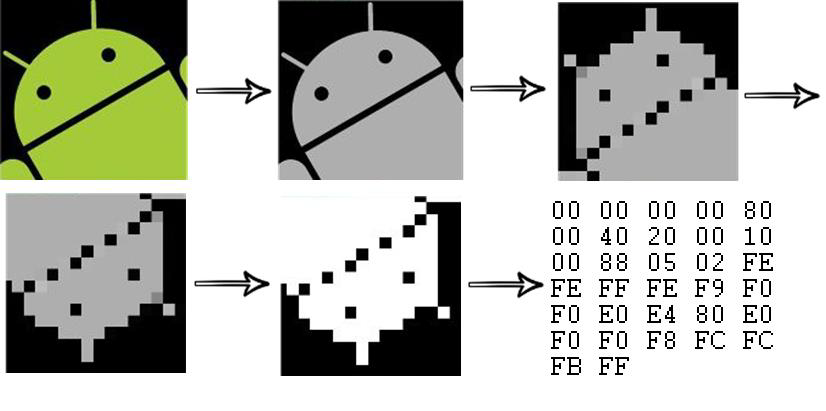
This hash algorithm works in four steps:
Step 1: Grayscale: Colors (RGB) are converted to grayscale (0x00 to 0xFF)
Step 2: Resize: Image is resized to target size e.g. 16×16 pixels
Step 3: Flip: Image is flipped horizontally and vertically until the brightest quarter of the image is in the top left corner
Step 4: Binarize: Convert grayscale pixels to black and white pixels using a threshold
In the following image, an example image is hashed using these four steps:
I still like the component and think it was a good addition to CrypTool 2. Clearly, the bachelor students got good grades for the project. Other results were the “Image processor”, the “Transcripor”, and the “Watermark Creator” in CrypTool 2 :-).
Today, I also createad a YouTube video about perceptual hashing. Here, I also show the “ImageHash” component of CrypTool 2 . You may watch it here:
Nils
[1] Steinebach, Martin. “Robust hashing for efficient forensic analysis of image sets .” International Conference on Digital Forensics and Cyber Crime. Springer, Berlin, Heidelberg, 2011