This is the third cipher of Félix-Marie Delastelle, a French hobby cryptographer, which I implemented in CrypTool 2. Delastelle published the four-square cipher in his book “Traité Élémentaire de Cryptographie“. He wrote the book in 1901 but it was published after Delastelle’s death in 1902.
The four-square cipher is a bigraphic monoalphabetic substitution cipher. Bigraphic means, that it always encrypts two plaintext letters at the same time. The cipher uses four Polybius squares, two of which are created using keywords.
Key Generation – Preparing the Four Polybius Squares
First, you have to prepare the four polybius squares. Let’s assume our keywords are “secret” and “keyword”:

Here, we created the second and third polybius squares using the previously chosen keywords. To create one of these polybius squares, the corresponding keyword is first written into the square from left to right and top to bottom. Here, if a letter occurs more than once, we omit it. In our example, we do not write the second “E” of “secret” again in the square. After writing the keyword, we fill the rest of the square with the remaining alphabet letters, which we did not already use for the keyword. After we created the second and third square, we fill the first and fourth square just with the alphabet. Since all the squares have only 25 positions, our alphabet consists of only 25 letters. Delastelle used “I” = “J” and did not include a “J” in his alphabet.
How Encryption works
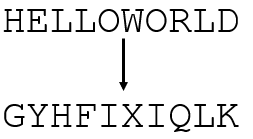
Now, we can encrypt a plaintext using our four polybius squares. Here, for example we want to encrypt “HELLOWORLD”. To do so, we search the letter “H” in the first square and the letter “E” in the fourth square:
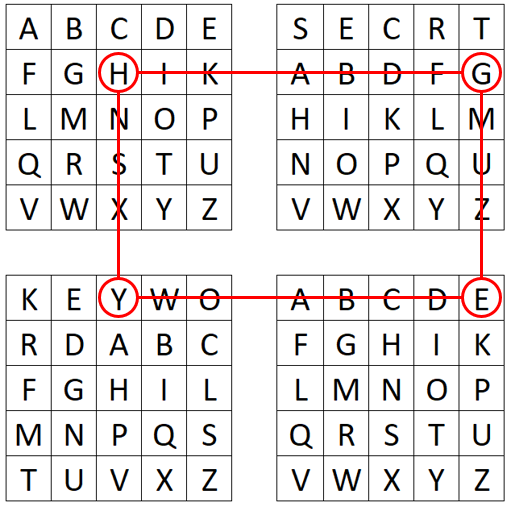
We create a connected “rectangle” where “H” is the upper corner and “E” is the lower corner. Now, we find our ciphertext letters in the two other corners of the so-created rectangle. Here, we encrypt the “H” by “G” and the “E” by “Y”. We continue encrypting our plaintext using this method to obtain the complete ciphertext:
To decrypt a given ciphertext, we just reverse the process. We look up the ciphertext letters (pair-wise) in the second and third square and find our plaintext letters in the first and fourth square.
Keyspace Size and Unicity Distance Computation
We compute the keyspace size by k = 25! * 25! = 2^167.36. This is, because we have to fill two polybius squares and a single polybius square has 25! possibilities to be filled with 25 letters.
We compute the unicity distance U by
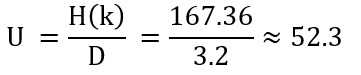
Here, H(k) is the entropy of the keyspace and D is the redundancy of the language (here English). From the English Wikipedia: “In cryptography, unicity distance is the length of an original ciphertext needed to break the cipher by reducing the number of possible spurious keys to zero in a brute force attack”. In our case, we need more than 53 letters to be able to obtain only one valid plaintext.
A YouTube Video about the Four-Square Cipher
I also created a YouTube video about the four-square cipher (and how you can use it in CrypTool 2). Watch it here:

If I use four random alphabets in those four squares, does that make the cipher more secure?
Also, if I rotate those squares after each letter, in a clockwise fashion, does that enhance security?
Hiho,
Yes, random alphabets would not allow a dictionary attack, therefore making the cipher stronger and increase the keyspace.
Rotating the alphabets after each letter would also strengthen the security since you create a polyalphabetic cipher this way.
Greetings,
Nils
Is there a difference between rotating and Transposing or are they the same thing? If different, which one is easier to solve ?
Hiho,
Rotation is just a special case of transposition, and a very weak one. If you know that only rotation was used, you only have to test n rotations, where n is the number of letters in your alphabet. The transposition of the alphabet gives you n! transpositions, which is a very large number of alphabets to test…:-)
Greetings,
Nils