In the linguistic study of written languages, a syllabary is a set of written symbols that represent the syllables or (more frequently) moras (basic timing unit in the phonology of some spoken languages) which make up words.
William F. Friedman and Lambros D. Callimahos present in “Military Cryptanalytics – Part 1” a Syllabary cipher or Syllabary square on page 250. The American Cryptogram Association (ACA) also defines the Syllabary cipher as part of their list of ciphers:
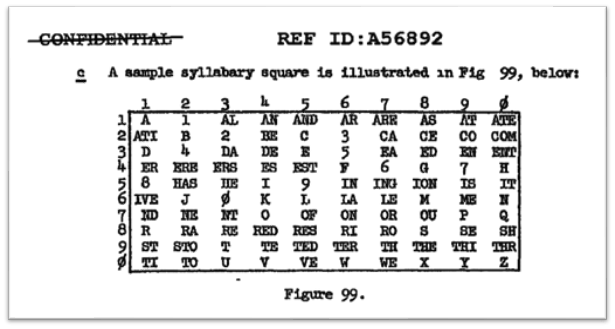
April 1956, by Friedman and Callimahos
Klaus Schmeh mentions a cipher he calls Crypto Number Table and also presents a challenge on his online blog. The crypto number table is in fact the Syllabary cipher.
How does the Cipher Work?
The Syllabary cipher uses a 10×10 table that contains letters, syllables from a given language, and digits:
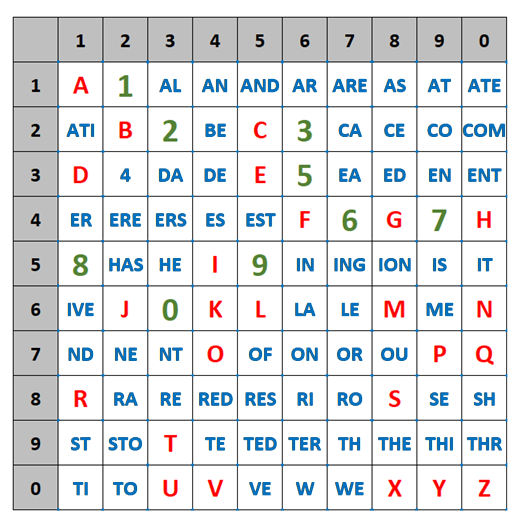
Basic ideas of the cipher are to suppress letter frequencies and to remove word patterns by different spellings of same plaintext words in the ciphertext.
To encrypt a plaintext, the text is replaced by digits (coordinates) found on the top and left side of the table. Examples:
HELLO WORLD 1 → 53 65 65 74 06 77 65 31 12
You can find different ciphertexts encrypting the same plaintext:
SECRET → 88 35 25 81 35 93
SECRET → 89 25 83 93
To decrypt a ciphertext, you have to look up the plaintext element using the ciphertext symbol as coordinates.
Keying Schemes
There are three different keying schemes (also defined by ACA):
1. Keep table and modify digits on top and on the left of the table (based on a digit key, e.g. 10293847568475610293)
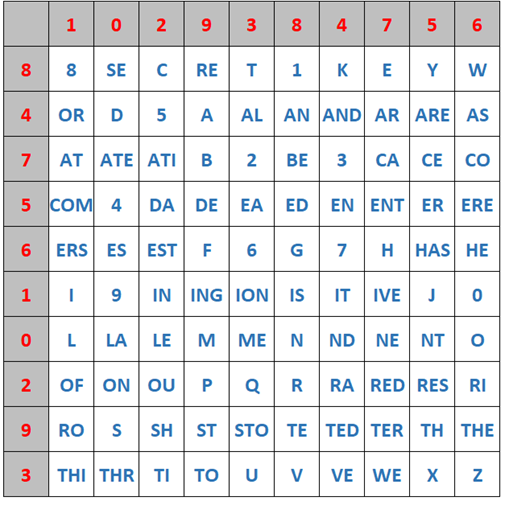
2. Keep digits on top and left of the table but reorder table (based on a keyword, e.g. 8SECRET1KEYWORD5)
3. Modify digits (based on a key) and reorder table (e.g. based on keyword)
A YouTube Video About the Cipher
I created a YouTube video about the cipher that you can watch here:
References
A blog post from Klaus Schmeh about the cipher: https://scienceblogs.de/klausis-krypto-kolumne/2018/09/01/can-you-break-the-crypto-number-table-challenge/
Friedman, William Frederick, and Lambros D. Callimahos. Military cryptanalytics. Vol. 2. Aegean Park Press, 1985.

I am trying to get in touch with George Lasry. I read with interest the story of his code breaking. My brother-in-law is Len Katz who was the classmate of George Lasry, perhaps his grandfather, at Yale in the late 1950s. I’d love to confirm and chat on email.
Hello Mr Horowitz,
You find George’s contact (email address) at the end of his video about the Mary Stuart ciphers.
See https://www.youtube.com/watch?v=kiL-QdQJPB0
Greetings,
Nils
Hiho,
I spoke to George. He says he is originally from France 🙂 So he is not the one you are looking for,
greetings,
Nils